COMP 100 Lecture Notes
Chapter 7, Part 2 : Network Security and Risks
Hacking
- hacking - purists call it cracking - exploiting
security weaknesses to break into a network or computer system for mischievous
or malicious purposes. Hackers are often caught through use of a honey
pot, an attractive decoy that lures the hacker in.
- White-hat hackers - get their thrills from the "chase". No intent to do damage, just want to
find security weaknesses in a system. May be very expert and may be hired by software companies to test the security of
their own software
- Black-hat hackers - out for destruction and theft
Identity Theft
How can someone "steal" your identity? Let's focus on those that involve computers
- shoulder surfing - look over your shoulder when computing in lab or public to get ID and password. Low-tech but effective.
- spyware - software that gathers information about your computer usage without
your knowledge and transmits that information to the thief. It can, for instance, collect keystrokes as you
type in credit card info or ID and passwords. Also has harmless uses for advertising.
- Note: Spyware is not to be confused with cookies, which are little files that a web site puts on your
hard drive to keep track of whether or how you have used that web site in the past. Web sites use cookies
to do things like greet you by name even when there is no login. Cookies are useful because HTTP
is a stateless protocol. That means that every request to a web server is independent of those
that precede it even from the same browser.
- phishing (not to be confused with
the jam band Phish) is email that pretends to be from
bank/EBay/PayPal/whoever requests that you verify account information online and provides a link.
The link as displayed may appear legit, but clicking it takes you to fraudulent site.
Email reader may display true URL when you cover mouse over the link. Usually the true URL has
numeric IP address (e.g. 223.29.147.9) instead of server name.
- packet sniffer - Ethernet NIC is capable of capturing all packets that pass through the "party line". If
you happen to be on the same party line then data you send/receive could be intercepted by "packet sniffing" software.
- fraudulent business on the web that will request credit card information for purchase. Your
liability limited to $50 but consider the additional hassles.
- other non-technical methods, like dumpster-diving to find discarded but unshredded
credit card solicitations and the like.
Malicious software: malware
- viruses : has become a catch-all term
- original meaning: malware that requires an agent or action to replicate
- typically arrives via email or download, and is harmless until activated
- effects may range from harmless (humorous display) to annoying (sends itself to everyone
in your address book) to devastating (wipes out your hard drive)
- platform-specific, usually targeted to Microsoft OS or applications due to
near-monopoly
- worms
- self-replicating without intervention
- can spread worldwide in minutes
- many worms exploit buffer overflow vulnerability that some programs have
- program and data co-exist in memory as binary
- buffer is data storage set aside to hold input
- input deliberately crafted to be longer than buffer - overflow
- the overflow replaces the current program with a new one that carries out malicious behavior
- first Internet worm was in 1988, released by Cornell student Robert Morris
- trojan horses - trusted program that also performs malicious function. Spyware is
an example -- you download and install a freeware or shareware program that includes the spyware component.
It may spread itself as a virus does.
| Name comes from story (possibly mythical) about Greek siege of Troy.
A large wooden horse, filled with Greek soldiers, was left at the gates
of Troy as "peace offering". The Trojans brought it in then proceeded
to celebrate. After they had passed out drunk, the soldiers climbed
out of the horse, opened the city gates, and the remaining Greek army
entered and conquered Troy. |
- denial of service (DOS) attacks - such attacks target Web servers. Massive numbers
of faked client requests targeted at the same server are generated very rapidly. The server can't keep
up and the service becomes unavailable to legitimate clients (users).
- distributed denial of service (DDOS) attacks - a DOS attack that comes from
many different clients simultaneously. Such clients are called zombies because they are
everyday networked computers like yours and mine that have been infected with the DDOS software
without our knowledge.
How do you get malware via the network?
- email attachments
- downloads - software that you download and install may contain virus or trojan horse
- "drive-by download" - downloaded without your knowledge when
you visit a malicious web site or click a malicious pop-up
- Internet port scan. Every Internet service has a designated "port" number in the range 0-65535. This allows multiple services
to be active at the same time. Email uses Port 25, HTTP (web) uses Port 80, etc. It is possible for a hacker to access your
computer via one of these ports if it is not protected.
How can you prevent this?
- Install and use antivirus software service, with frequent or automatic updates
- Your computer must have antivirus software to use the Otterbein network, which will scan your computer when
you connect to make sure. More information on residence hall
computers at www.otterbein.edu/its/reshalls/
- Antivirus software works by looking for bit patterns (signatures) that exist in known viruses. These patterns change
constantly, so your software has be updated constantly. It is a real cat-and-mouse game.
- Install and use firewall software (organization servers use firewall hardware too)
- Your ISP may provide these as a benefit or at extra cost
- Wired and wireless routers also include some firewall protection -- NAT is a technique in which router intercepts outgoing
requests and changes sender's ID to an alias, then only responses addressed to the correct alias are allowed in
- Windows Firewall is included in Windows 7, Vista, and XP Service Pack 2
- Install and use anti-spyware software.
- Windows Defender is included in Windows 7 and Vista, and XP Service Pack 2
- Spybot Search and Destroy
(www.safer-networking.org) is very good and free.
- Beware: some products advertised as anti-spyware will in fact install spyware!
- Some Anti-virus products include anti-spyware; others do not
- It can be hard to distinguish between "bad spyware" (tracks your actions in order to steal from you)
and "good spyware" (tracks your actions in order to enhance your online experience by showing you things it
thinks may interest you)
- Don't make your folders and devices open to sharing.
- Be cautious when installing free downloaded software
- Don't open email attachments from strangers
- Be cautious of unexpected email attachments even from those you know (message could have been produced by virus)
WiFi Risks
WiFi is really convenient but beware of the risks
Risks of using WiFi away from your home network
Here's a screen capture I made in November 2009 while waiting in Chicago O'Hare airport (for yet-another late flight)
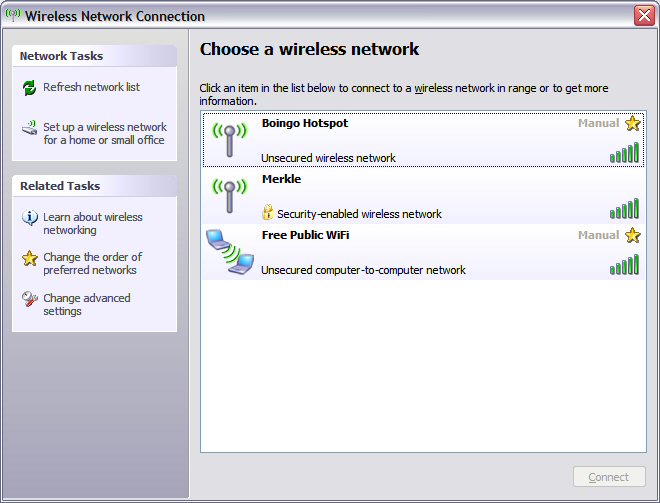
My WiFi card has detected three available wireless networks:
- Boingo - a commercial service provided by the airport. Announced regularly over the PA.
Not free. "Unsecured wireless network", which means that communications between your Wifi and the access point are
not encrypted (disguised; more on this below). Note: HTTPS web pages are still secure because HTTPS has its own encryption
applied by your browser before the packet leaves your computer.
- Merkle - I have no idea whose network this is, but it is "Security-enabled". That means you have to
have a special code called a key to communicate with it. Wifi communications are encrypted and you need the
key to decrypt. So better security.
- Free Public WiFi - This is the one to avoid at all
costs! Notice it says "Unsecured computer-to-computer network". Wifi-enabled
laptops can form temporary ad hoc wireless networks that consist
only of each other. These are called "computer-to-computer networks" and can
be really cool among friends for game-playing and the like. But if you connect
to this network, you are connected directly to some stranger's laptop. You
may be able to get an Internet connection via their laptop, but their
laptop will also receive all the packets that yours sends out - packet sniffing!
Risks of operating a Wireless Access Point or Router on your home network
- Your neighbors can use your Internet bandwidth for free - how you feel about this depends on
how well you know and get along with your neighbors. The Wifi range is limited to a couple hundred feet but
does not cut off at your apartment wall or property line.
- Strangers can park near your house and connect to your network. This is like leaving the
doors to your room/house unlocked. An invitation for hackers.
- Wireless transmissions happen inside the reach of your firewall, which guards only the wired interface between
your network and the Internet.
Securing your home wireless access point or router
- Turn off your access point when no one is home.
- Position the access point to minimize range extension beyond your property.
- Change the access point's admin password - You perform network administration through your web browser
and have to login first. But the default password is factory installed and hackers know the defaults.
- Change the SSID - The SSID is the "name" of your wireless
access point. It is set to a default at the factory, and hackers know all
the default names.
- Disable SSID broadcast - By default, your access point will transmit its SSID. This
is the signal that laptops detect so they can display available networks as shown in the figure. You can
turn this feature off. A laptop will still be able to connect, but it has to know what your SSID is.
- Use encryption - Several types of encryption are available. The most common are WEP and the
better and preferred WPA. You establish a key, and anyone wishing to connect has to use that key.
- Restrict access to specific computers - Every NIC has a unique ID installed by the factory,
called its MAC address. You can program your access point to accept connections only from
specified MAC addresses. This is called MAC filtering. I do this with my home network.
User authentication methods restrict access based on:
- something you know (password, ID, special information such as childhood pet's name).
Problematic; people do not design passwords well (we use common or easily guessed words)
- something you have (smart card, device with ever-changing password, flash key)
- physical attribute- biometrics (fingerprint, retinal scan, facial structure)
Secure Internet transmission of sensitive data
Have you made a credit card purchase from a Web site?
When a web page prompts you to enter sensitive information, look at the protocol part of
the URL (upper left corner of browser window). If it is https://
then the information will be encrypted for transmission, using a secure transmission
service called Secure Sockets Layer (SSL). If it is
regular http://, do not continue the transaction online.
Cryptography
Encryption methods hide information through combination of
- substitution - substitute one character for another
- transposition - scramble the order of characters
Special knowledge called the key is required to encrypt and decrypt
There are two basic strategies concerning keys
- secret key (aka symmetric) cryptography is where both sender and
intended receiver must know the key and no one else. The "same" key is used to both
encrypt and decrypt
- public key (aka asymmetric) cryptography is where there
is both a public key, which everyone knows, and a private key, which only
its owner knows. The public key, which is used to encrypt, is different than
the private key, which is used to decrypt. First developed in the 1970s.
Classic example of secret key cryptography is Caesar Cipher
- alphabetic substitution is based on rotational shift.
- two part key: direction and number of positions to shift
- Example cipher: if encrypted by right shift 3, A is replaced by D, B replaced by E, ... Z replaced by C.
- Example message using that cipher: HDVB WR EUHDN
- not secure since it can be broken by brute force (limited number of possible keys)
- How to be sure that both sender and receiver know the key, but no one else does?
This is weakness of any private key cipher.
Classic example of public key cryptography is RSA or variation
- here's how it works, to securely transmit from Alice to Bob.
- Alice has public encryption key EAlice and private decryption key DAlice
- Bob has public encryption key EBob and private decryption key DBob
- Alice encrypts the message using public key EBob and sends it
- Bob receives the message and decrypts it using private key DBob
- can also use it for digital signature. How can Bob be sure the message
really came from Alice, and not from Trudy?
- Alice encrypts the message as above
- Alice then applies her private key DAlice before transmitting
- When Bob receives the message, he first applies Alice's public key EAlice
- The E will undo the D, just like the D will undo the E
- If the message had come from someone other than Alice, it would not work
- commonly used variation is PGP (Pretty Good Privacy)
E-commerce simply would not be possible without public key cryptography! HTTPS is
based on it also.
Criminals and terrorists also benefit, since no one can read their encrypted
messages
